How To Remotely Access IoT Devices Via SSH, Web, And Download: A Comprehensive Guide
Imagine this: you're sitting in a cozy café miles away from home, sipping your favorite coffee, and suddenly you need to check on your IoT devices back at the office or home. Sounds impossible? Nope! With SSH, web access, and secure downloads, you can easily control and manage your IoT devices remotely. Whether you're a tech enthusiast or a professional, this guide will show you how to do it seamlessly.
Accessing IoT devices remotely has become a necessity in today's fast-paced world. Whether it's monitoring security cameras, managing smart home appliances, or controlling industrial equipment, being able to access your devices from anywhere is crucial. But how exactly do you do that? That's where SSH, web interfaces, and secure download methods come into play.
Now, don't freak out if you're not a tech wizard. This article breaks down the process step by step, so even if you're new to the world of IoT, you'll walk away with the knowledge to set up remote access like a pro. So grab your favorite snack, get comfy, and let's dive into the world of remotely accessing IoT devices.
- Mckinley Richardson Nude Leak The Truth Behind The Sensation
- Alice Roseblum Nudes A Comprehensive Look At The Misunderstood Narrative
Why Remotely Access IoT Devices?
Before we jump into the nitty-gritty, let's talk about why remote access to IoT devices is such a big deal. IoT devices are everywhere—smart thermostats, security systems, industrial sensors, and more. Having the ability to control these devices from anywhere gives you flexibility, convenience, and peace of mind. Plus, it saves time and resources. Who wouldn't want that, right?
Here's a quick breakdown of the benefits:
- Increased efficiency: No need to physically be near the device to make changes.
- Enhanced security: Monitor and manage security systems remotely.
- Cost savings: Reduce travel expenses by managing devices from afar.
- Convenience: Access your devices anytime, anywhere.
But hold up—before you start setting everything up, it's important to understand the tools and methods you'll need. That's where SSH, web interfaces, and secure downloads come in.
- Jatt Movie Download Hdhub4u Your Ultimate Guide To Streaming And Downloading
- Who Is Michael Consuelos Partner The Untold Story Behind The Spotlight
Understanding SSH for IoT Devices
SSH, or Secure Shell, is like a superhero in the world of remote access. It's a cryptographic network protocol that allows you to securely connect to a device over an unsecured network. Think of it as a secret tunnel that keeps your data safe while you're accessing your IoT devices remotely.
Here's why SSH is so awesome:
- Encryption: All data sent through SSH is encrypted, keeping it safe from prying eyes.
- Authentication: SSH uses public and private keys to ensure only authorized users can access the device.
- Command-line access: You can run commands directly on the device as if you were physically there.
Now, setting up SSH might sound intimidating, but trust me, it's not that bad. We'll cover the setup process in detail later on, but for now, just know that SSH is your go-to tool for secure remote access.
Setting Up SSH for IoT Devices
Alright, let's get down to business. Setting up SSH for your IoT devices isn't as complicated as it seems. Here's a step-by-step guide to help you get started:
Step 1: Enable SSH on Your IoT Device
Most IoT devices come with SSH disabled by default for security reasons. You'll need to enable it manually. Here's how:
- Log in to your IoT device's management interface.
- Look for the "Services" or "Security" section.
- Enable SSH and save the changes.
Pro tip: Make sure to change the default SSH port (usually 22) to something less common to enhance security.
Step 2: Generate SSH Keys
SSH keys are like your digital ID card. They allow you to authenticate without needing a password every time. Here's how to generate them:
- Open a terminal or command prompt on your computer.
- Run the command:
ssh-keygen -t rsa -b 4096. - Follow the prompts to create and save your keys.
Once you've generated your keys, you'll need to copy the public key to your IoT device. This is usually done by editing the ~/.ssh/authorized_keys file on the device.
Using Web Interfaces for Remote Access
While SSH is great for command-line access, sometimes you just want a user-friendly interface. That's where web interfaces come in. Many IoT devices come with built-in web interfaces that allow you to manage and control them through a browser.
Here's how to set up a web interface for your IoT device:
Step 1: Check for Built-in Web Access
Most modern IoT devices have a web interface enabled by default. Simply connect to the device's network and open a browser. Enter the device's IP address in the address bar, and voilà—you're in!
Step 2: Secure Your Web Interface
Web interfaces can be a security risk if not properly secured. Here are some tips to keep your device safe:
- Change the default username and password.
- Enable HTTPS to encrypt your connection.
- Restrict access to specific IP addresses if possible.
By following these steps, you can enjoy the convenience of a web interface without compromising security.
Downloading Data Securely from IoT Devices
Sometimes, you need to download data from your IoT devices. Whether it's log files, sensor data, or configuration backups, doing so securely is crucial. Here's how to do it:
Option 1: Use SCP (Secure Copy Protocol)
SCP is a command-line tool that allows you to securely transfer files between your computer and an IoT device. Here's how to use it:
- Open a terminal or command prompt.
- Run the command:
scp username@device_ip:/path/to/file /local/path. - Enter your password or use SSH keys for authentication.
Option 2: Use SFTP (Secure File Transfer Protocol)
SFTP is similar to SCP but offers more functionality, such as the ability to browse directories. You can use SFTP through a terminal or a graphical client like FileZilla.
Pro tip: Always verify the integrity of downloaded files using checksums to ensure they haven't been tampered with.
Best Practices for Secure Remote Access
Now that you know how to remotely access your IoT devices, let's talk about best practices to keep everything secure:
- Use strong, unique passwords for all devices.
- Enable two-factor authentication whenever possible.
- Keep your devices and software up to date with the latest security patches.
- Monitor access logs regularly for any suspicious activity.
By following these practices, you can minimize the risk of unauthorized access and ensure your IoT devices remain secure.
Common Challenges and How to Overcome Them
As with anything in life, remotely accessing IoT devices comes with its own set of challenges. Here are some common issues and how to solve them:
Challenge 1: Network Connectivity Issues
Solution: Make sure your IoT device is connected to a stable network. If you're accessing it from outside your local network, consider setting up a VPN for a more reliable connection.
Challenge 2: Security Concerns
Solution: Follow the best practices we discussed earlier. Additionally, consider using a firewall to restrict access to your devices.
Challenge 3: Limited Resources
Solution: If your IoT device has limited processing power, consider using lightweight SSH clients or web interfaces to reduce the load.
By addressing these challenges head-on, you can ensure a smooth and secure remote access experience.
Tools and Software You Need
Having the right tools can make all the difference when it comes to remotely accessing IoT devices. Here are some recommendations:
- SSH clients: PuTTY (Windows), Terminal (Mac/Linux).
- Web browsers: Chrome, Firefox, or any modern browser.
- File transfer tools: SCP, SFTP, or FileZilla.
Make sure to choose tools that are compatible with your operating system and devices.
Real-World Applications of Remote IoT Access
So, how exactly can you apply this knowledge in real life? Here are a few examples:
Application 1: Smart Home Management
With remote access, you can control your smart home devices from anywhere. Adjust the thermostat, turn off lights, or check security cameras—all from your smartphone.
Application 2: Industrial Automation
In industrial settings, remote access allows engineers to monitor and control equipment without needing to be on-site. This saves time and reduces costs.
Application 3: Agriculture
Farmers can use IoT devices to monitor soil moisture, weather conditions, and crop health. Remote access enables them to make informed decisions without having to physically visit the fields.
These applications demonstrate the versatility and importance of remotely accessing IoT devices.
Conclusion
Remotely accessing IoT devices via SSH, web interfaces, and secure downloads is not only possible but also essential in today's connected world. By following the steps and best practices outlined in this guide, you can set up a secure and efficient remote access system for your devices.
So, what are you waiting for? Take action today! Try setting up SSH on one of your IoT devices, explore its web interface, and download some data securely. Share your experience in the comments below, and don't forget to check out our other articles for more tech tips and tricks.
Table of Contents
- Why Remotely Access IoT Devices?
- Understanding SSH for IoT Devices
- Setting Up SSH for IoT Devices
- Using Web Interfaces for Remote Access
- Downloading Data Securely from IoT Devices
- Best Practices for Secure Remote Access
- Common Challenges and How to Overcome Them
- Tools and Software You Need
- Real-World Applications of Remote IoT Access
- Conclusion
- Jameliz Onlyfans Leaked The Untold Story You Need To Hear
- Billy Idols Daughter What Does She Do A Closer Look At Her Life And Career
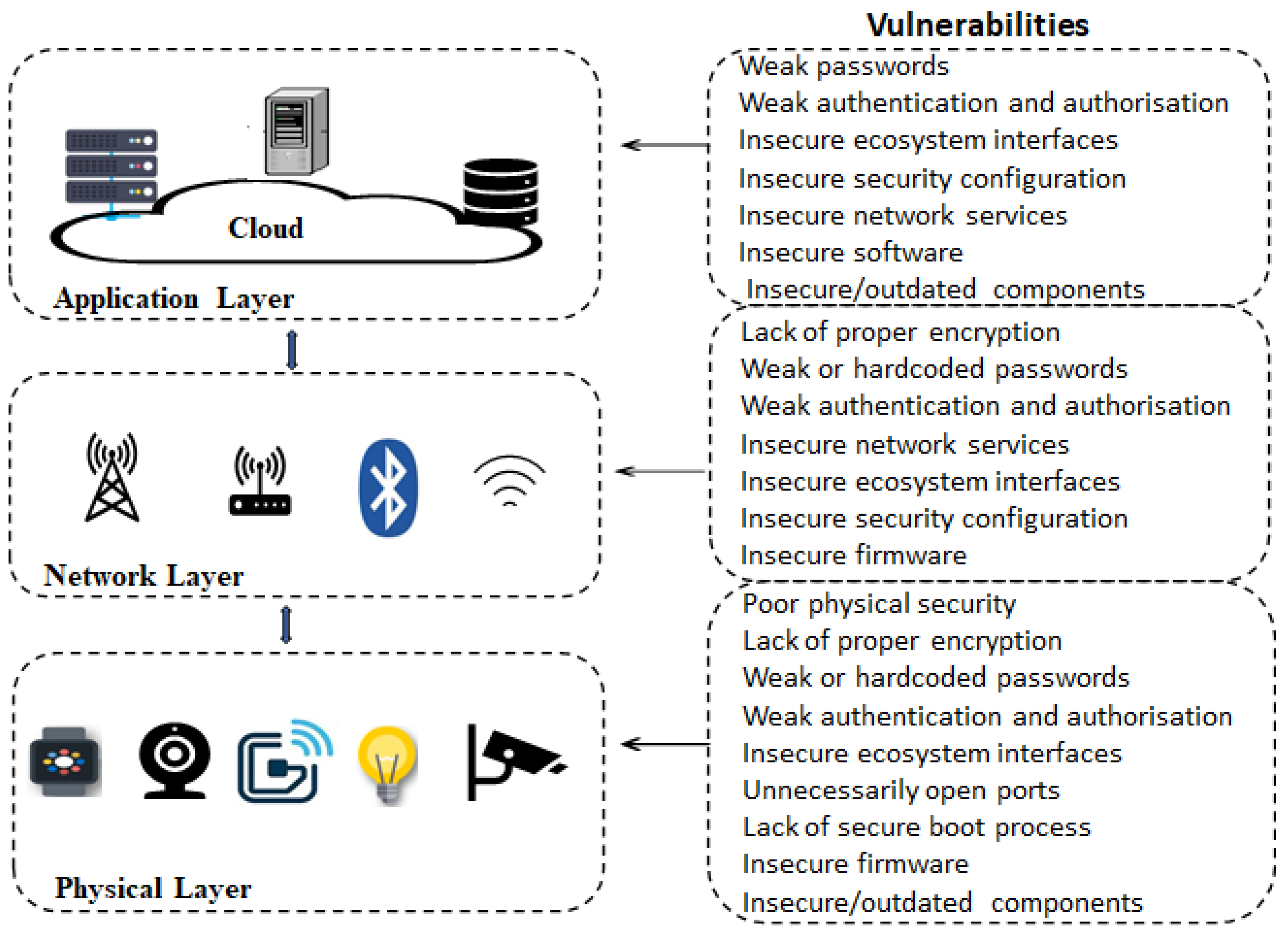
Electronics Free FullText Analysis of Consumer IoT Device

Sensors Free FullText An IoTBased Smart Home Automation System
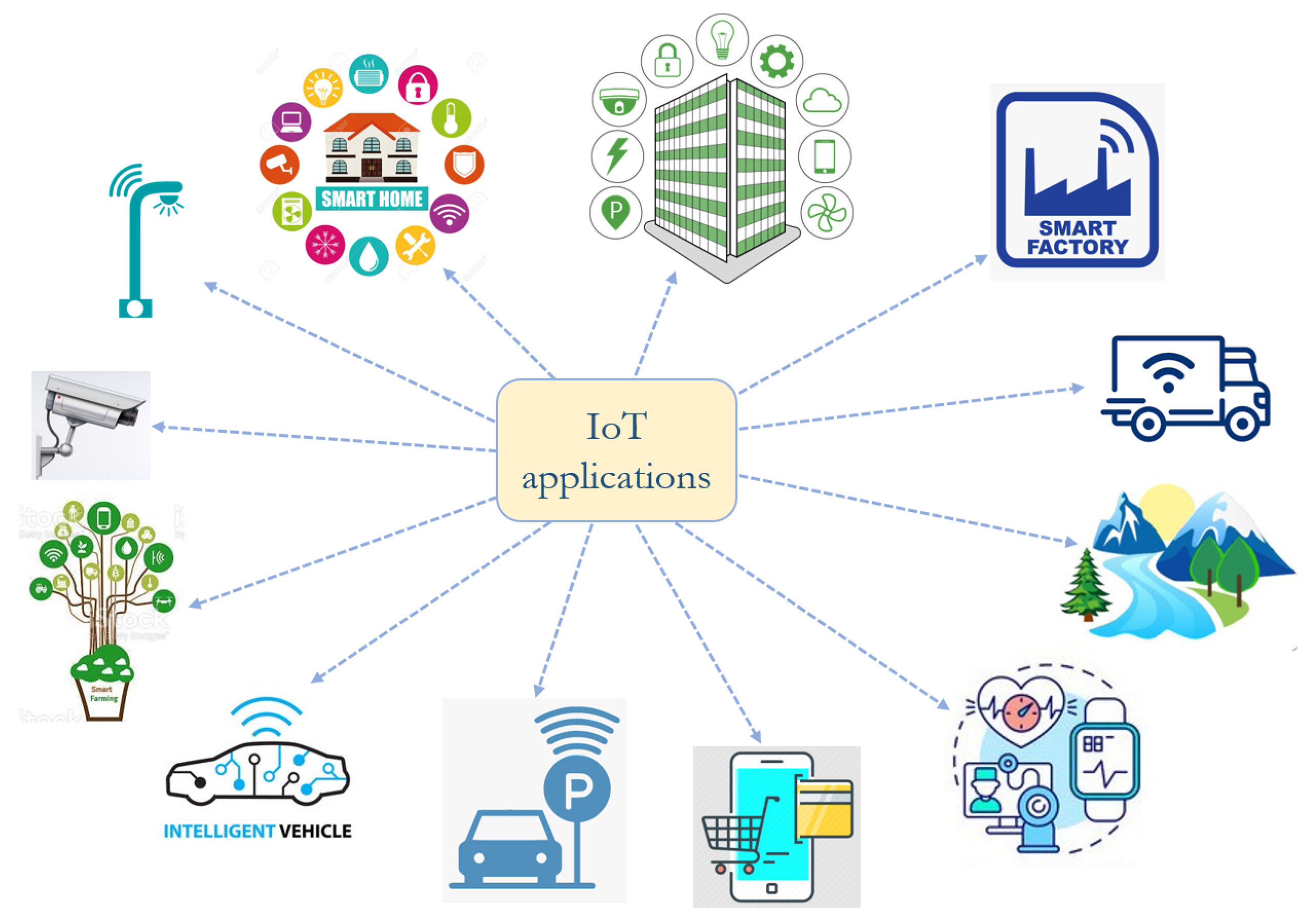
IoT Free FullText A Holistic Overview of the of Things